Category: Security
-
Hashing & Data integrity
Hashing is the process of using a hash function in computing and cryptography that converts data into a fixed-sized string of characters, typically a sequence of letters and numbers. For example, the operating system on your pc stores passwords as hashes. The operating system uses a hashing function to hash your password and stores it
-
Google updates Chrome — fixes around 20 vulnerabilities.
The latest Chrome version, 142, released by Google on October 28th, includes patches to fix several documented vulnerabilities, some of which are high-severity. The update includes permission to block local network access from public/local websites. Chrome now blocks websites from sending requests to local network devices (like routers, printers, or software running on your machine)
-
Python script to check if VDB databases are updated in Cisco FMC
To check if VDB databases are updated in Cisco FMC and print the results to an Excel file using Python, you can use the following approach: 1.Access Cisco FMC through API: Use the Cisco FMC API to retrieve the VDB database information. You can find more details about the API in the Cisco FMC API documentation.
-

How to set up AnyConnect VPN in Cisco Firepower Threat Defense (FTD)
here’s a step-by-step guide on how to set up AnyConnect VPN in Cisco Firepower Threat Defense (FTD): Prerequisites Step 1: Configure Remote Access VPN Policy Step 2: Configure Client Profiles Step 3: Upload AnyConnect Images Step 4: Configure Remote Access VPN Connection Step 5: Save and Deploy Policy Step 6: Verify AnyConnect Client Installation Additional
-

Deleting a Stuck Deployment Notification in Cisco FMC
Its frustrating it can be when a Cisco Firepower Threat Defense (FTD) deployment gets stuck and keeps showing up in notifications. Let’s sort it out this issue:
-
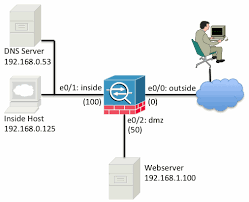
How to use Packet Tracer on Cisco ASA
Packet tracer feature used to verify the security mechanisms as packet moves from one interface to another in a cisco ASA firewall. By this we can troubleshoot why the traffic is not working in the firewall or whether we created the rule correctly or not A typical series of security features tested might look like
-
Introduction To Cisco ASA Firewall
Introduction In computer networking, Cisco ASA 5500 Series Adaptive Security Appliances, or simply Cisco ASA, is Cisco’s line of network security devices introduced in May 2005, that succeeded three existing lines of popular Cisco products: Cisco PIX, which provided firewall and network address translation (NAT) functions ended sale on 28 July 2008. Cisco IPS 4200
-
Introduction to Firewall
WHAT IS FIREWALL A firewall is a network security device, either hardware or software-based, which monitors all incoming and outgoing traffic and based on a defined set of security rules it accepts, rejects or drops that specific traffic. Accept : allow the traffic Reject : block the traffic but reply with an “unreachable error” Drop
-
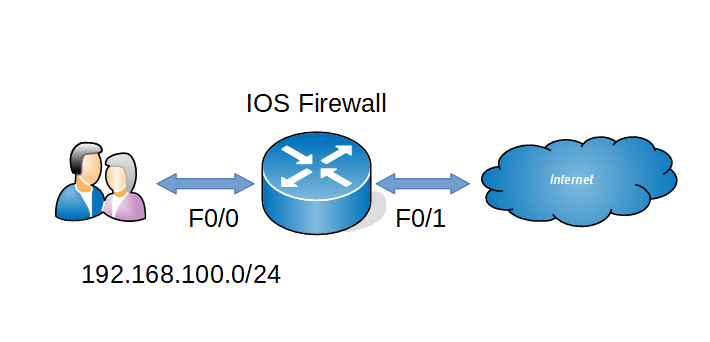
How to configure CBAC in Cisco router
Context Based Access Control (CBAC) is an IOS firewall feature set similar like RACL, RACL is basically inspect L2- L4 layers only but CBAC has the capability of inspecting application layer traffic. Now we can see the configurations Step 1 : Create one ACL to deny all incoming traffic from the internet Step 2 :
-
How To Configure Reflexive ACL in Cisco Router .
RACL is a type of ACL which will permit only the external traffic which is originated from inside and it will block all other external traffic . RACL will keep the session table of the outgoing traffic and it will check the external traffic with that particular session table . Find below for the configurations